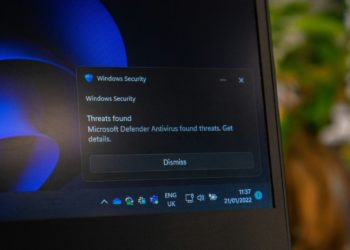
Email has been around for decades and it’s not going anywhere. It’s still how deals start, invoices move and customer relationships grow. But it’s also where attackers are quietly finding new ways in. Even after years of investment in advanced threat detection and user training, email remains the most common way to compromise an organization. Not because the tools are bad, but because attackers have learned that it’s much easier to trick people than to break through code.
That shift from targeting systems to targeting people has turned the inbox into one of the most critical and least controlled attack surfaces in business.
From Firewalls to Inboxes – The Shift in Attack Surfaces
There was a time when defending a company meant setting up firewalls, antivirus software and network gateways. These were used to define the perimeter and everything inside felt safe. That worked when people worked from offices, used corporate devices and connected through managed networks.
Now things have changed. Employees log in from coffee shops, personal laptops and phones. Cloud platforms hold more data than local servers ever did. Attackers know that too. They don’t waste time trying to bypass routers when a believable email from “finance@yourcompany.co” can do the job. It’s faster, cheaper and far more effective.
Phishing has grown into an industry of its own. You can literally buy phishing kits that come with realistic templates, fake websites, and hosting. Some even include 24/7 support for the criminals using them. That’s how professional this ecosystem has become. Traditional defenses cannot stop this kind of deception because it doesn’t rely on code but rather on trust.
How Broken Trust in Email Threatens Brand Credibility
The danger is not just about someone clicking on a bad link. It’s about what happens after. When a customer receives a fake email that looks like it came from your company, they don’t just lose money, they also lose confidence and trust.
For example, if a supplier gets tricked into paying a fake invoice or a customer receives a phishing email using your logo, what do they remember? Not that an attacker was clever, but that your brand felt unsafe.
Even if you’re not directly at fault, that association sticks with your brand identity. Over time, people become hesitant. They double check every message. They stop engaging as easily. Open rates drop and marketing teams start wondering why their carefully crafted emails aren’t performing anymore.
This erosion of trust hurts silently. It doesn’t show up in a security dashboard, but it shows up in customer behavior and once that credibility slips, it’s hard to win back.
Regulated industries face an even bigger challenge. Beyond reputation damage, there are compliance questions, like did you take steps to authenticate your domain? Were verification standards like SPF, DKIM, and DMARC configured correctly? Regulators don’t care that the spoofed email didn’t come from your servers; they care whether you did enough to prevent it.
That’s what makes trust the new currency of communication. Once it’s broken, everything else starts to lose value.
Why Every Enterprise Should Rethink Inbox Security
Email security is still treated as just a technical checklist by most organizations till date. Their checklist might include things like blocking spam mails, quarantining malware, and filtering suspicious attachments. It works to a point. But those tools were built for a time when threats were mostly about bad links or infected files. Today’s attackers are smarter. They use legitimate platforms, believable content and stolen identities.
The conversation has to move beyond filtering out bad emails. It needs to focus on confirming the good ones. That’s where verification comes in. Instead of trying to detect every potential scam, companies should start proving authenticity with every legitimate message they send. When a recipient opens an email, there should be something visual, technical, or both that says, “Yes, this is really from us.”
This idea is already gaining ground. Verified mark certificates, for instance, allow trusted brands to display their logo right inside supported inboxes. Combined with domain based authentication, it creates a visible layer of assurance that helps people know who they’re communicating with.
The goal should be to make every email look and feel consistently genuine. To achieve this, a few steps need to be completed, like having a clear domain usage policy, proper branding, and awareness across all departments. Employees are less likely to fall for impersonations if they know what an authentic internal email looks like. This applies to your customers as well. When they are able to spot the difference between a real invoice and a fake one, you prevent fraud and keep building loyalty.
This shift changes how we think about inbox security. It’s not just part of IT’s job anymore but a part of brand management. Protecting your email channel means protecting your reputation.
Conclusion
Email isn’t the weakest link because it’s old, but it’s the weakest link because it relies on trust. And attackers know exactly how to exploit that. Protecting inboxes is no longer just about stopping bad content; it’s about making authenticity clear and consistent at every level. The inbox has become where relationships are tested. It’s where your brand speaks directly to someone, and whether they trust that voice determines how secure your communication truly is.


![7 Best POS Software in the UK [2026 Edition]](https://todaynews.co.uk/wp-content/uploads/2026/02/7-Best-POS-Software-in-the-UK-2026-Edition-360x180.png)



















































![7 Best POS Software in the UK [2026 Edition]](https://todaynews.co.uk/wp-content/uploads/2026/02/7-Best-POS-Software-in-the-UK-2026-Edition-120x86.png)

![7 Best POS Software in the UK [2026 Edition]](https://todaynews.co.uk/wp-content/uploads/2026/02/7-Best-POS-Software-in-the-UK-2026-Edition-350x250.png)