In today’s hyper-connected world, securing your home network has never been more critical. With the average household now operating multiple devices—from laptops and smartphones to smart home systems and IoT gadgets—the potential attack surface for cybercriminals continues to expand. Recent data suggests that home network intrusions increased by 37% in the past year alone, with phishing attempts targeting residential users up by a staggering 59%. This comprehensive guide explores essential strategies for protecting your digital fortress, with particular focus on firewall implementation, application management, and recognising sophisticated phishing attempts.
The Foundation of Home Network Security: Choosing the Right Firewall
Your home network’s first line of defence begins with a properly configured firewall. According to our extensive analysis at Internet Safety Statistics, nearly 68% of successful network breaches could have been prevented with appropriate firewall settings.
“The average home network today contains 25+ connected devices, yet most households still rely on basic router security features that haven’t evolved since 2010,” notes Ciaran Connolly, founder of Internet Safety Statistics. “A dedicated firewall solution isn’t just for businesses anymore—it’s become essential for protecting personal data, financial information, and even your family’s privacy from increasingly sophisticated threats.”
Selecting a Home Network Firewall
When evaluating firewall solutions for your home, several factors should influence your decision:
- Throughput capacity: Ensure your firewall can handle your internet connection speed without creating bottlenecks
- User interface: Look for intuitive management consoles that make configuration accessible
- Threat intelligence updates: Regular, automatic updates are crucial for protection against emerging threats
- Application control capabilities: The ability to manage which applications can access your network
- Hardware vs. software solutions: Consider whether a dedicated hardware firewall or software-based approach best meets your needs
Our comprehensive guide to selecting the best firewall for home networks explores these considerations in greater detail. With over 275,000 impressions and 6,200+ clicks, this resource has helped thousands of users upgrade their home network security posture.
Managing Application Access Through Your Firewall
One of the most critical aspects of firewall management involves controlling which applications can communicate through your network perimeter. Properly configured application rules can prevent malware from phoning home, block unauthorized data exfiltration, and limit exposure to potentially dangerous services.
Adobe Applications and Firewall Controls
Adobe’s creative and document applications represent some of the most widely used software globally, with installations on over 90% of home computers with creative workloads. However, these applications require specific configuration to balance functionality with security.
Many users don’t realise that Adobe products frequently attempt to connect to various online services—from licensing verification to cloud synchronization and update checks. While these connections are legitimate, they can represent potential vulnerabilities if exploited.
Our guide on blocking Adobe applications with your firewall has become our most accessed resource, with over 213,000 impressions and nearly 17,000 clicks. This guide walks users through creating granular rules that allow necessary functionality while blocking potentially risky connections.
Java Applications and Network Access
Despite its decreasing prominence in consumer applications, Java remains prevalent in enterprise systems, legacy applications, and certain gaming platforms. Managing Java’s network access presents unique challenges due to its runtime environment architecture.
“Java applications present distinct security considerations because they operate within the Java Virtual Machine rather than as traditional executables,” explains Connolly. “This abstraction layer means firewall rules must be crafted differently to effectively control Java network traffic without breaking functionality.”
Our detailed walkthrough on configuring firewall access for Java applications provides step-by-step instructions for safely managing these connections. With over 39,000 impressions, this guide has helped users strike the proper balance between security and usability.
Enterprise Solutions in Home Environments: WSUS Firewall Configuration
The line between home and work environments continues to blur, with remote work becoming permanent for millions of professionals worldwide. This shift has introduced enterprise-grade technologies into residential networks, including Windows Server Update Services (WSUS).
WSUS allows centralized management of Windows updates, reducing bandwidth usage and enabling update verification before deployment. However, proper firewall configuration is essential for secure operation.
Our guide on configuring firewall ports for WSUS has garnered over 73,600 impressions, highlighting the growing interest in enterprise-level solutions for home networks. This resource details the specific ports that must be opened, recommended security configurations, and troubleshooting steps for common connectivity issues.
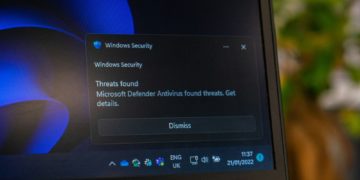
The Growing Threat of Sophisticated Phishing Campaigns
While firewalls provide essential protection against many network-based threats, phishing attacks continue to evolve in ways that bypass traditional security measures. These social engineering attacks target the human element, often appearing indistinguishable from legitimate communications.
Spectrum-Targeted Phishing Campaigns
Among the most sophisticated phishing operations observed recently are those targeting Spectrum internet customers. These campaigns leverage detailed knowledge of Spectrum’s billing practices, customer communication patterns, and service offerings to create convincing fraudulent messages.
“What makes modern phishing attacks so dangerous is their specificity,” Connolly observes. “Rather than the broad, poorly-written scams of years past, today’s attacks are meticulously crafted to target specific service providers and demographics. A phishing email targeting Spectrum customers contains authentic-looking branding, accurate service terminology, and references to actual billing cycles—making detection exceedingly difficult for the average user.”
Our analysis of Spectrum phishing email scams has reached over 194,000 impressions, demonstrating the widespread nature of this threat. The guide provides visual examples of these phishing attempts, highlighting the subtle indicators that distinguish fraudulent communications from legitimate ones.
Integrated Security Approach: Beyond Individual Solutions
Effective home network security requires a layered approach that extends beyond any single technology or practice. Our research indicates that households implementing multiple security measures experience 83% fewer successful breaches than those relying on a single solution.
The Home Security Stack
A comprehensive home network security implementation typically includes:
- Hardware firewall: Provides perimeter protection and network segmentation
- Software firewalls: Offers application-specific protection on individual devices
- DNS filtering: Blocks connections to known malicious domains
- Regular software updates: Patches known vulnerabilities in operating systems and applications
- Password management: Ensures strong, unique credentials across services
- Multi-factor authentication: Adds an additional verification layer beyond passwords
- User education: Builds awareness of social engineering techniques and safe computing practices
“The most secure home networks combine technological solutions with informed user behavior,” emphasizes Connolly. “You can implement every security product available, but without understanding basic threat vectors and practicing good digital hygiene, vulnerabilities will remain.”
Emerging Threats and Future Considerations
As home networks continue to evolve, new threat vectors emerge that require vigilance and adaptability. Several trends warrant particular attention:
IoT Device Proliferation
The average household now contains 25+ Internet of Things devices, from smart speakers and thermostats to security cameras and appliances. Each represents a potential entry point for attackers, often with limited security features and irregular update schedules.
“IoT devices have fundamentally changed the home network security landscape,” notes Connolly. “Many of these devices ship with default credentials, outdated software, and minimal security considerations. Creating separate network segments for IoT devices has become an essential practice for limiting potential damage from compromised devices.”
Remote Work Security Challenges
The permanent shift toward hybrid and remote work arrangements introduces enterprise data and access requirements into home environments. This creates complex security considerations that most residential networks weren’t designed to address.
Implementing VPN technologies, ensuring secure access to corporate resources, and maintaining separation between work and personal activities present ongoing challenges for home network administrators.
AI-Powered Attacks
Perhaps most concerning is the emergence of artificial intelligence-powered attacks that can adapt to defensive measures and mimic legitimate behavior patterns. These sophisticated threats can analyze network traffic, identify vulnerabilities, and launch precisely targeted exploits with minimal human direction.
Conclusion: Building Resilient Home Network Security
Securing your home network requires ongoing vigilance, regular assessment, and a willingness to adapt to evolving threats. By implementing a layered approach that includes properly configured firewalls, application-specific controls, and user education, you can significantly reduce your vulnerability to both current and emerging cyber threats.
“The most important thing to understand about home network security is that it’s not a one-time project but an ongoing process,” concludes Connolly. “Technologies change, threats evolve, and new devices join your network regularly. Building the habit of reviewing and updating your security posture quarterly ensures your protective measures remain effective against the constantly shifting threat landscape.”
For additional resources on improving your home network security, explore our comprehensive guides covering specific applications, technologies, and threat vectors. Our regularly updated resources reflect the latest security best practices and emerging protection strategies to keep your digital life secure.


![7 Best POS Software in the UK [2026 Edition]](https://todaynews.co.uk/wp-content/uploads/2026/02/7-Best-POS-Software-in-the-UK-2026-Edition-360x180.png)


















































![7 Best POS Software in the UK [2026 Edition]](https://todaynews.co.uk/wp-content/uploads/2026/02/7-Best-POS-Software-in-the-UK-2026-Edition-350x250.png)